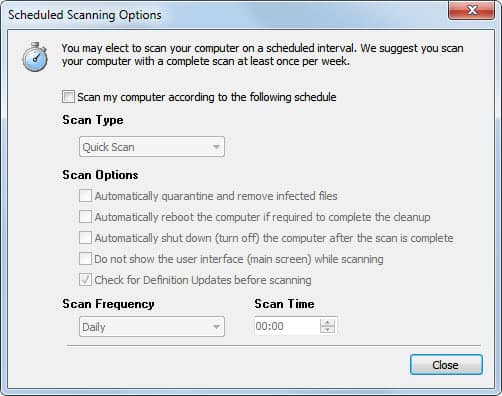
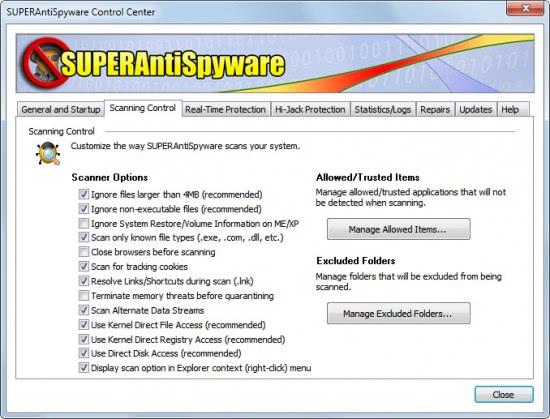
No one working in network security can complain that the issue has been ignored by the press. Between Stuxnet, WikiLeaks server attacks and counterattacks, and the steady march of security updates from Microsoft and Adobe, the topic is being discussed everywhere. IT workers who have discovered that consolidation, off-shoring, and cloud computing have reduced job opportunities may be tempted to take heart in comments such as Tom Silver’s (Sr. VP for Dice.com) claim that “there is not a single job position within security that is not in demand today.”This and similar pronouncements by others paint a rosy picture of bottomless security staff funding, pleasant games of network attack chess, and a bevy of state-of-the-art security gadgets to address threats. Maybe.
In these challenging times, separating hype from visionary insight may be a tall order. Yet it’s important to strike a sensible balance, because there are problems both with underestimating the problem as well as in overhyping the value of solutions. This situation became readily apparent when making a list of overlooked threats for the upcoming year. The task of sorting through the hype must not become a cause that only managers will be inspired to take up.
Table A summarizes a modest list of security threats that are likely to be overlooked in the coming year. The list thus adds to the mélange of worry-mongering, but at least the scenarios are plainly labeled as worst case scenarios.
1. Insider threat
Millions of dollars can be spent on perimeter defenses, but a single employee or contractor with sufficient motivation can easily defeat those defenses. With sufficient guile, such an employee could cover his tracks for months or years. Firms such as Symantec Vontu have taken a further step and characterized the insider threat issue as “Data Loss Prevention” (DLP). Also in this category are attacks on intellectual property, which tend to be overlooked in favor of more publicized losses.
2. Tool bloat backlash
Recent TSA changes to airport security demonstrate that the public’s appetite for security measures has limits. The same is true for network security. As demands for more and more tools taking an increasingly larger percent of the IT budget mount, backlash is inevitable. Many tools contribute to a flood of false positives and may never resist an actual attack. There is a network security equivalent of being overinsured.
| Threat Area | Worst Case Scenarios |
| 1. Insider Threat | Enterprise data including backups destroyed, valuable secrets lost, and users locked out of systems for days or even weeks. |
| 2. Tool Bloat Backlash | Decision-makers become fed up with endless requests for security products and put a freeze on any further security tools. |
| 3. Mobile Device Security | A key user’s phone containing a password management application is lost. The application itself is not password-protected. |
| 4. Low Tech Threats | A sandbox containing a company’s plan for its next generation of cell phone chips is inadvertently exposed to the public Internet. |
| 5. Risk Management | A firm dedicates considerable resources to successfully defend its brochure-like, ecommerce-less web site from attack, but allows malware to creep into the software of its medical device product. |
| 6. SLA Litigation | Although the network administrator expressed reservations, a major customer was promised an unattainable service level for streaming content. The customer has defected to the competition and filed a lawsuit. |
| 7. Treacheries of Scale | A firm moves from a decentralized server model to a private cloud. When the cloud’s server farm goes offline, all users are affected instead of users in a single region. |
Table A. Worst Case Scenarios for Overlooked Network Security Threats
3. Mobile device security
There’s lots of talk about mobile device security, but despite prominent breaches employing wireless vectors, many enterprises haven’t taken necessary precautions.
4. Low-tech threats
Addressing exotic threats is glamorous and challenging. Meeting ordinary, well-understood threats, no matter how widespread, is less interesting and is thus more likely to be overlooked. Sandboxes, “test subnets,” and “test databases” all receive second class attention where security is concerned. Files synchronized to mobile devices, copied to USB sticks, theft of stored credentials, and simple bonehead user behaviors (”Don’t click on that!”) all fit comfortably into this category. Network administrators are unlikely to address low tech threats because more challenging tasks compete for their attention.
5. Risk management
Put backup and disaster recovery in this category, but for many, having servers with only one NIC card or relying upon aging, unmonitored switches and exposed cable routing are equally good use cases. Sadly, most organizations are not prepared to align risks with other business initiatives. To see where your organization stands in this area, consider techniques such as Forrester’s Lean Business Technology maturity for Business Process Management governance matrix.
6. SLA Litigation
Expectations for service levels are on the rise, and competitive pressures will lead some firms to promise service levels that may not be attainable. Meanwhile, expectations for service levels by the public continue to rise.
7. Treacheries of scale
There will be the network management version of the Quantas QF32 near-disaster. Consequences of failure, especially unanticipated failure, increase as network automation is more centralized. Failure points and cascading dependencies are easily overlooked. For instance, do network management tools identify SPOF? A corollary is that economies of scale (read network scalability) lead directly to high efficiency threats - that is, risks of infrequent but much larger scale outages.
What’s a network administrator to do? Address the issues over which some control can be exerted, and be vigilant about the rest. Too much alarm-sounding is likely to weaken credibility.
 Christmas is coming, and you're about to have a ton of time off. Some of that time will be spent energetically tearing apart beautifully-wrapped gifts, and eating food is certainly next on the list of priorities. Obviously you have to play with your new gifts (or put on your new socks), but after that... after the postprandial sofa-surfing grunts and burps and farts... well, there isn't a whole lot you can do.
Christmas is coming, and you're about to have a ton of time off. Some of that time will be spent energetically tearing apart beautifully-wrapped gifts, and eating food is certainly next on the list of priorities. Obviously you have to play with your new gifts (or put on your new socks), but after that... after the postprandial sofa-surfing grunts and burps and farts... well, there isn't a whole lot you can do.